Overview
Top users by critical activity on the Action Items dashboard shows a prioritized view of the users associated with the most critical and high severity file events. Top users by critical activity only shows events that occurred outside your trusted domains or in unapproved cloud destinations.
Risk severity is determined by Incydr's Proactive Risk Identification and Severity Model (PRISM), which analyzes 250+ risk indicators about data, users, and destinations to provide weighted severity scores. For more information about risk indicators and severity, see Risk settings reference.
For more information about dashboards, see:
Considerations
-
Add trusted activity and data connections to focus your investigations on higher-risk file activity. Adding trust settings allows Incydr to show only untrusted file events on security event dashboards, user profiles, and alerts, reducing your total file event volume. All file activity is still visible in Forensic Search.
- For permissions, licensing, and visibility considerations, see Action Items dashboard reference.
Top users by critical activity
To view top users by critical activity:
-
Sign in to the Incydr console.
- Select Dashboards > Action Items.
Top users by critical activity appears in the upper right.
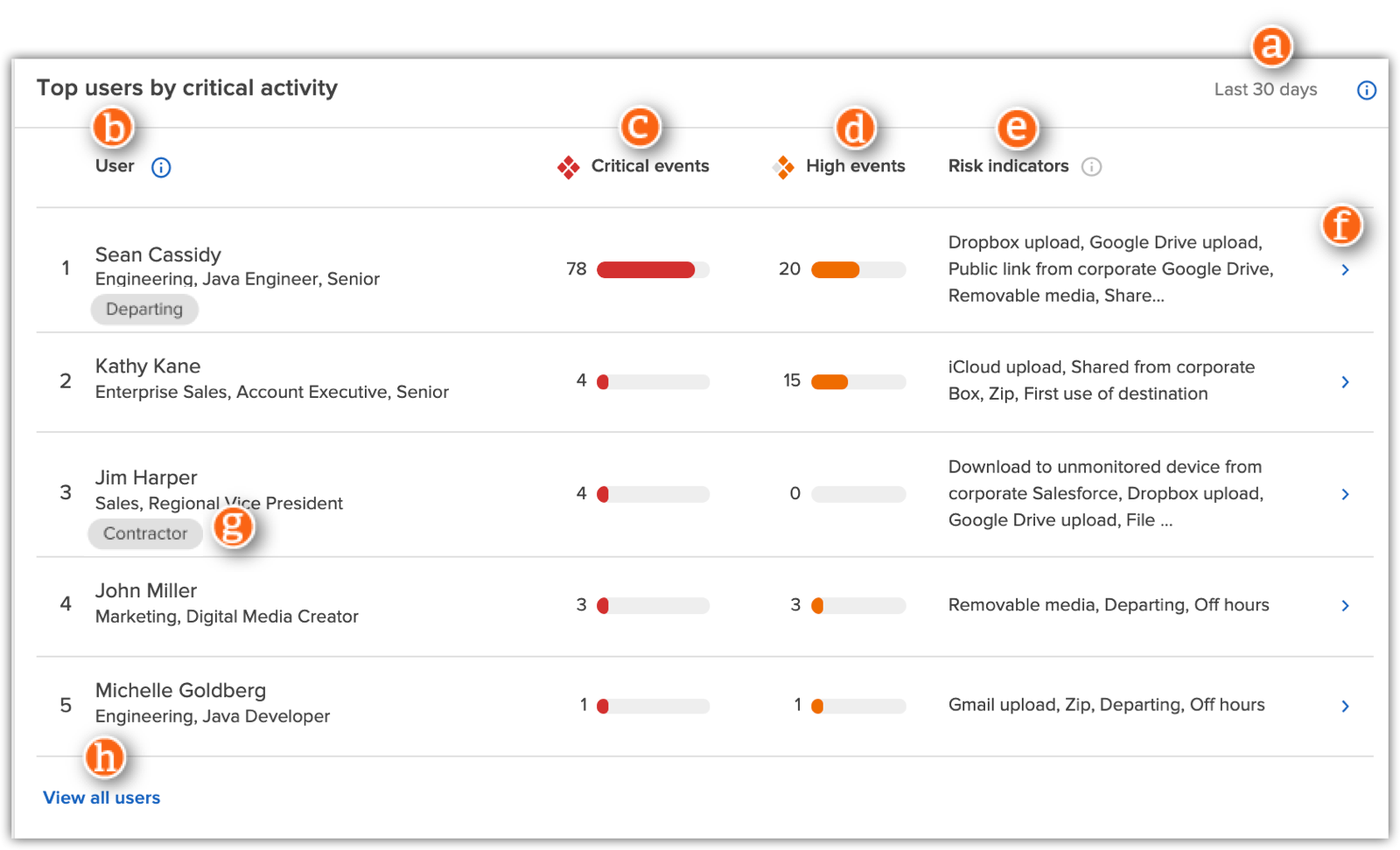
| Item |
Description |
| a |
Selected time frame |
Shows the time frame the file activity occurred in.
|
| b |
User |
Displays a summary of the employee's information, including:
- Name
- Department*
- Title*
-
Watchlists the employee has been added to
*Displays this information if your Incydr environment uses provisioning. For more information, see Provision user attributes to Incydr.
Click the user's name to open their User profile.
|
| c |
Critical events
|
Displays file events with a PRISM score of 9+.
The PRISM score is based on the sum of all risk indicators applied to an event.
For more information about risk indicators and severity, see Risk settings reference.
|
| d |
High events |
Displays file events with a PRISM score of 6-9.
The PRISM score is based on the sum of all risk indicators applied to an event.
For more information about risk indicators and severity, see Risk settings reference.
|
| e |
Risk indicators |
Shows the risk indicators that apply to a user's file events. For more information about risk indicators, see Risk settings reference.
Risk indicators are listed in the following order:
- Destination risk indicators, alphabetically
- File risk indicators, alphabetically
- User risk indicators, alphabetically
|
| f |
View details 
|
Click to see more details about the file activity. |
| g |
Watchlist badge |
Indicates if the employee is on a watchlist for closer monitoring and shows the name of the watchlist. |
| h |
View all users |
Click to see a list of all users in your Incydr environment. |
View details
From Top users by critical activity, click View details to see more information about the user's file activity.
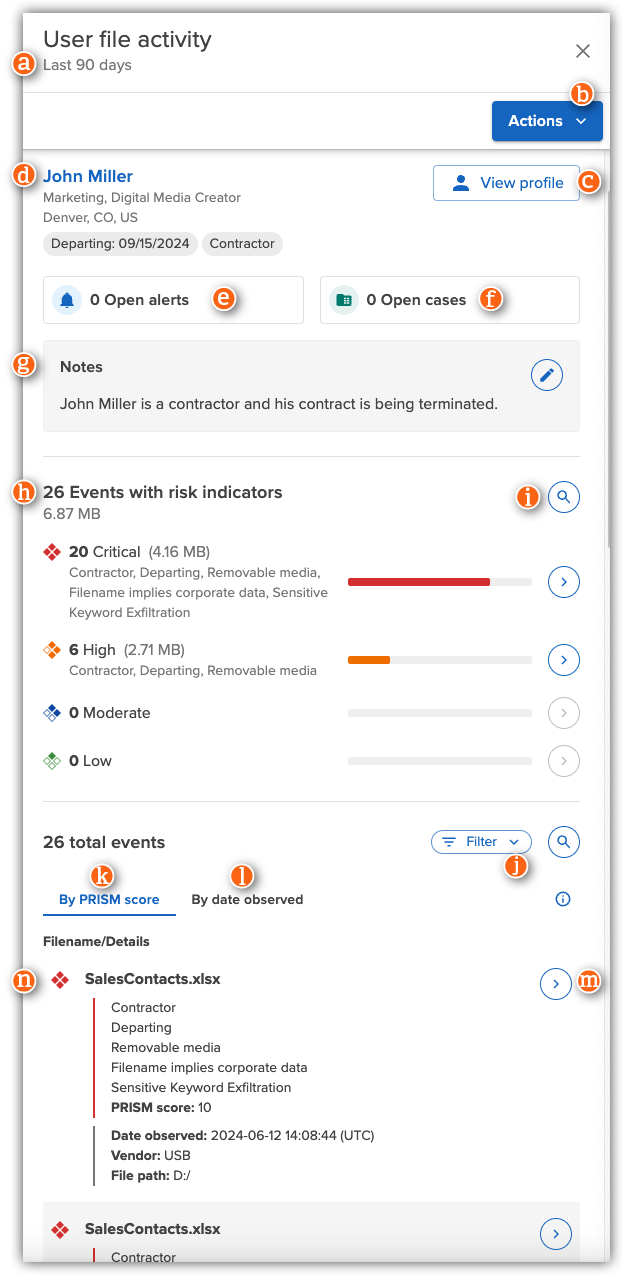
| Item |
Description |
| a |
Selected time frame |
Shows the time frame the file activity occurred in. Change the time frame in the upper-right corner of the screen.
|
| b |
Actions |
Click the Actions menu and do one of the following:
- Select Add to watchlists to add the user to one or more watchlists for closer monitoring. If the user is already on a watchlist, select Edit watchlists to change the user's current watchlist memberships.
- In Alerts, select Send email to email the user requesting more information about their activity. Customize the message as needed before you send it.
- Select Send user an Instructor lesson to send a lesson to the user.
- Select a custom action.
- Incydr Flows connect other systems or workflows to Incydr. These integrations can add contextual information about users and orchestrate response controls.
- Custom actions are only available if your organization has worked with Incydr Professional Services to set up Incydr Flows and if you have the correct role.
Visibility of actionsYou are only shown actions that you are allowed to access based on your Incydr role and your organization's product plan. For example:
|
| c |
View profile |
|
| d |
User |
Displays a summary of the employee's information, including:
- Name
- Department*
- Title*
-
Watchlists the employee has been added to
*Displays this information if your Incydr environment uses provisioning. For more information, see Provision user attributes to Incydr.
|
| e |
Open alerts |
Shows the number of alerts the user has triggered during the selected time frame that are in the Open, In progress, or Pending response status. Click to see the user's alerts. |
| f |
Open cases |
Shows the number of cases with the Open status for which the user has been added as the subject of the case. Click to see the user's cases. |
| g |
Notes |
Do one of the following:
- Click Add
 to add more details to the user's profile. to add more details to the user's profile.
- Click Edit
 to modify existing notes. to modify existing notes.
Notes are limited to 1000 characters.
|
| h |
Events with risk indicators |
Displays counts of each file event severity with associated risk indicators.
For more information about risk indicators, see Risk settings reference.
|
| i |
Investigate in Forensic Search 
|
Click to see more details about the file events in Forensic Search. Learn more about using Forensic Search. |
| j |
Filter |
Click to show filters that allow you to see events based on risk indicator or watchlist. To remove a selected filter, click it again. |
| k |
By PRISM score |
Click to show file events by PRISM score in descending order. |
| l |
By date observed |
Click to show file events by the date the event occurred with latest events on top. |
| m |
View details 
|
Click to view details about the file event. For detailed descriptions of each field, see File event metadata. |
| n |
Filename/Details |
Shows filename, risk indicators, PRISM score, and other details about the file event.
If the filename is shown as a blue hyperlink, you can download the file from this location. If the filename is not a blue hyperlink, you may be able to download the file in Forensic Search.
To view all file events with more detail, click Investigate in Forensic Search  . .
|
Related topics
Comments
0 comments
Please sign in to leave a comment.