Overview
The Source risk indicator activity graph on the Exfiltration dashboard shows all of the file events that occurred across your organization where files were acquired from a source likely to contain company data.
For more information about dashboards, see:
Considerations
Source risk indicator activity
To view source risk indicator activity:
-
Sign in to the Incydr console.
- Select Dashboards > Exfiltration.
- Scroll down to Source risk indicator activity.
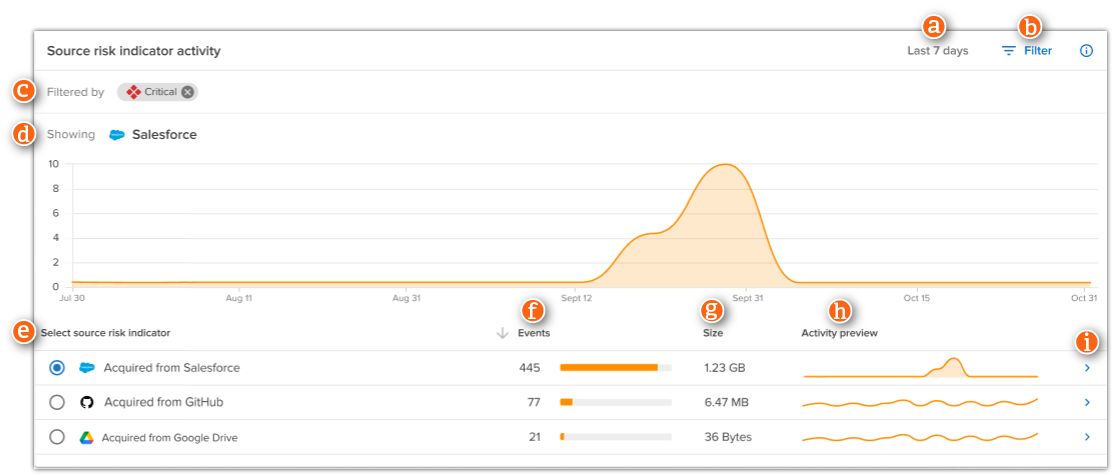
| Item |
Description |
| a |
Selected time frame |
Shows the time frame the file activity occurred in. Change the time frame in the upper-right corner of the page.
|
| b |
Filter |
Click to filter the graph and events in the table by:
|
| c |
Filtered by |
Shows the filters currently applied to the data shown in the graph as well as the data available in the source indicators. Click the "x" on a filter to remove it. |
| d |
Showing |
Lists the source risk indicator you are viewing.
|
| e |
Select source risk indicator
|
Select a source risk indicator to see where the file was sent and its associated risk.
Source risk indicators are applied to file events where the file came from a source likely to contain company data.
|
| f |
Events |
Number of file events associated with the risk indicator for the selected time frame. |
| g |
Size |
Total size of files involved with the file activity. |
| h |
Activity preview |
Shows a visual representation of file activity for the selected time frame. |
| - |
Investigate in Forensic Search 
(not pictured)
|
Click to view the events in Forensic Search. |
| i |
View event details 
|
Click to view more information about the file events. |
Filter
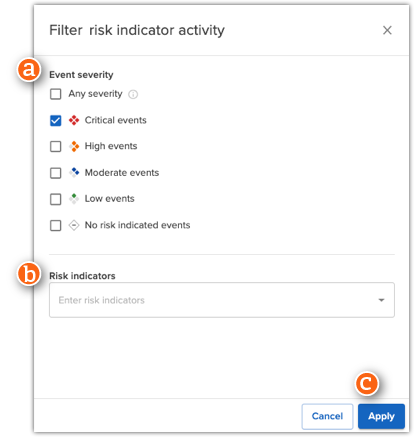
| Item |
Description |
| a |
Event severity |
Select one or more file severities to view in the graph. No risk indicated events are file events that have a risk score of zero. For more details about calculating risk severity, see Risk settings reference. |
| b |
Risk indicator |
Click to select one or more risk indicators to view in the graph. For more details about what risk indicators are and how they're applied, see Risk settings reference
|
| c |
Apply |
Click Apply to filter the information in the graph by your criteria or click Cancel. |
Related topics
Comments
0 comments
Please sign in to leave a comment.